If you are living in Los Angeles, it would not come as a surprise to note that car accidents are quite common and can happen any day. What would be surprising though is to know that these car accidents that happen in the city every 40 hours can prove fatal. That is why Safe Roads USA dubbed Los Angeles as the “deadliest city for traffic deaths” in the United States.
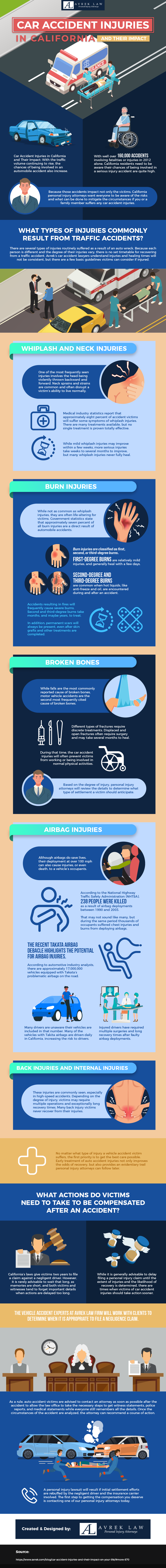
While many of these accidents are truly caused by unavoidable circumstances that are beyond anyone’s control, some of these accidents are caused by negligence, recklessness or utter disregard for traffic laws. What’s sad is that such accidents can be serious enough to result in physical injuries like whiplash, burns, broken bones, and even internal injuries. Victims of such injuries resulting from recklessness can get the assistance of an auto accident attorney, Los Angeles based preferably, to help them process a physical injury claim.
Dealing with such injuries can have a big impact on anyone involved in such accidents. Aside from the pain and suffering they incur; they can find themselves in great financial difficulties from their medical expenses and from their lack of income because of their inability to return to their jobs or businesses. Because of these, they are entitled to receive compensation from liable parties, but they would need the assistance of a reliable Los Angeles personal injury lawyer to help them.
Getting involved in such accidents can create a big impact on any person’s life, particularly if such incidents result in physical injuries. You can get a better understanding about these car accident injuries and gain insights on what you need to do should you get involved in one by going through the following blog post from Avrek Law Firm.